Kali Linux can be utilized for some things, however, it likely is best known for its capacity to penetration test, or "hack," WPA and WPA2 systems. There are many Windows applications that claim they can hack WPA; don't get them! They're simply tricks, utilized by proficient programmers, to draw amateur or wannabe programmers into getting hacked themselves. There is just a single way that programmers get into your system, and that is with a Linux-based OS, a remote card equipped for screen mode, and aircrack-ng or comparative. Likewise take note of that, even with these devices, WiFi breaking isn't for tenderfoots. Playing with it requires fundamental information of how WPA verification functions, and direct commonality with Kali Linux and its devices, so any programmer who accesses your system most likely is no tenderfoot!
Steps
Step-1
Start Kali Linux and log in, preferably as root
Step-3
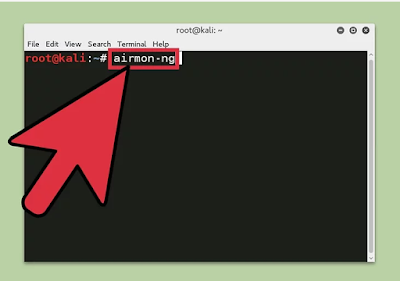
Disconnect from all wireless networks, open a Terminal, and sort airmon-ng. This will list the majority of the remote cards that help screen (not infusion) mode.

Step-2
Plugin your injection-capable wireless adapter (unless your computer card supports it).
|
Step-3
- In the event that no cards are recorded, take a stab at disconnecting and reconnecting the card and watch that it underpins screen mode. You can check if the card bolsters screen mode by writing ifconfig in another terminal, if the card is recorded in ifconfig, however doesn't appear in airmon-ng, at that point the card doesn't bolster it.
Step-4
Sort airmon-ng begin took after by the interface of your remote card. For instance, if yours is wlan0, your charge would be: airmon-ng begin wlan0.
- The "(screen mode enabled)" message implies that the card has effectively been put into screen mode. Note the name of the new screen interface, mon0.
Sort airodump-ng took after by the name of the new screen interface, which is most likely mon0.ce, mon0.
Step-6
Survey the Airodump comes about. It will now list the greater part of the remote systems in your general vicinity, and bunches of helpful data about them. Find your system or the system that you have authorization to infiltration test. Once you've recognized your system on the consistently populating list, hit Ctrl+C on your console to stop the procedure. Note the channel of your objective system.
Step-7
Step-7
Duplicate the BSSID of the objective system. Presently sort this summon: airodump-ng - c [channel] - bssid [bssid] - w/root/Desktop/[monitor interface]
- Supplant [channel] with the channel of your objective system. Glue the system BSSID where [bssid] is, and supplant [monitor interface] with the name of your screen empowered interface, (mon0).
- A total order should resemble this: airodump-ng - c 10 - bssid 00:14:BF:E0:E8:D5 - w/root/Desktop/mon0.
Step 8
Hold up. Airodump with now screen just the objective system, enabling us to catch more particular data about it. What we're truly doing now is sitting tight for a gadget to associate or reconnect to the system, driving the switch to convey the four-way handshake that we have to catch keeping in mind the end goal to split the watchword.
- Likewise, four records should appear on your desktop; this is the place the handshake will be spared when caught, so don't erase them! In any case, we're not by any means going to sit tight for a gadget to interface, no, that is not what anxious programmers do.
- We're really going to utilize another cool-device that has a place with the aircrack suite called aireplay-ng, to accelerate the procedure. Rather than sitting tight for a gadget to associate, programmers utilize this apparatus to compel a gadget to reconnect by sending deauthentication (deauth) bundles to the gadget, influencing it to imagine that it needs to reconnect with the switch. Obviously, all together for this device to work, there must be another person associated with the system in the first place, so watch the airodump-ng and sit tight for a customer to appear. It may require a long investment, or it may just take a moment before the first shows. In the event that none appear after a long hold up, at that point the system may be vacant right now, or you're to far from the system.
Step 9
Leave airodump-ng running and open a moment terminal. In this terminal, sort this summon: aireplay-ng – 0 2 – a [router bssid] – c [client bssid] mon0.
- The – 0 is an alternate way for the demise mode and the 2 is the quantity of deauth bundles to send.
- - a shows the entrance point (switch's) bssid; supplant [router bssid] with the BSSID of the objective system, for instance, 00:14:BF:E0:E8:D5.
- - c shows the customers BSSID. Supplant the [client bssid] with the BSSID of the associated customer; this will be recorded under "STATION."
- What's more, obviously, mon0 only means the screen interface; change it if yours is extraordinary.
- A total charge resembles this: aireplay-ng – 0 2 – a 00:14:BF:E0:E8:D5 – c 4C:EB:42:59:DE:31 mon0.
Step-10
Hit Enter. You'll see aireplay-ng send the bundles, and inside minutes, you should see this message show up on the airodump-ng screen! This implies the handshake has been caught, the secret word is in the programmer's hands, in some frame or another.
- You can close the aireplay-ng terminal and hit Ctrl+C on the airodump-ng terminal to quit checking the system, yet don't close it yet simply in case you require a portion of the data later.
- Starting now and in the foreseeable future, the procedure is altogether between your PC, and those four records on your Desktop. In reality, the .top one, that is important.
Step-11
Open another Terminal. Sort in this order: aircrack-ng - a2 - b [router bssid] - w [path to wordlist]/root/Desktop/*.cap
- - a is the strategy aircrack will use to break the handshake, 2=WPA technique.
- - b remains for bssid; supplant [router bssid] with the BSSID of the objective switch, as 00:14:BF:E0:E8:D5.
- - w remains for wordlist; supplant [path to wordlist] with the way to a wordlist that you have downloaded. For instance, you may have "wpa.txt" in the root organizer./root/Desktop/*
- .cap is the way to the .top document containing the secret word; the * implies trump card in Linux, and expecting there are no other .top records on your Desktop, this should work fine the way it is.
- An entire order resembles this: aircrack-ng – a2 – b 00:14:BF:E0:E8:D5 – w/root/wpa.txt/root/Desktop/*.cap.
Step-12
Sit tight for aircrack-ng to dispatch into the way toward splitting the secret word. In any case, it will just break it if the secret key happens to be in the wordlist that you've chosen. Once in a while, it's most certainly not. If so, at that point you can salute the proprietor on being "impervious," obviously, simply after you've attempted each wordlist that a programmer may utilize or make!








Comments
Post a Comment